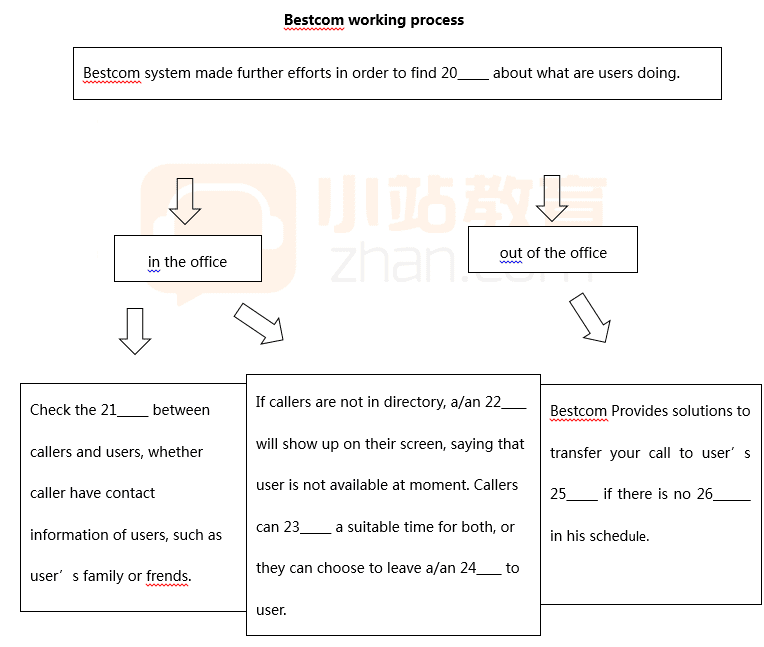
暗示词,即在做雅思阅读题过程中,按照平常划定位词去需找信息,并不容易获得关键信息,但是利用题目中的某些暗示能够较快速地知道题目要的答案大致在哪个地方,今天小编给大家带来了雅思阅读技巧之暗示词,希望能够帮助到大家,下面小编就和大家分享,来欣赏一下吧。
雅思阅读提分丨雅思阅读技巧之暗示词
一、解题暗示词是什么?
即在做题过程中,如果按照平常划定位词直接去搜索答案的方法不容易获得关键信息,利用题目中的某些暗示能够较快速地知道题目要的答案大致在哪个地方,大体是什么形式的。既然叫暗示,题目当中就不会有明显的大写或者数字,它只是通过题目中某些单词传递出一些重要的线索。所以,也需要同学们用心去发现、积累。
二、根据用法,解题暗示词主要可以分为以下几类:
1.形式暗示词
数字暗示词:most, high level of, amount, how much, price, cost, timing, percentage, proportion ...
大写暗示词:where, location, name, be called ...
特殊符号暗示词:be called, be named, be defined as ...
否定、消极暗示词:fail, miss, weaken, difficulty, problem, disruptive ...
极限暗示词:the most, no possible, limit, up to, never ...
2.结构暗示词
开头段暗示词:overview, origin, early history ...
中间段暗示词:examples, figure, data ...
结尾段暗示词:conclude, prediction, future, prospect ...
三、形式暗示词在剑桥雅思真题中的运用
1.真题还原:Cambridge 4 Test 1 Passage 1 Rainforests Question 10 short-answer matching
原题摘录:What was the most common response to the question about the importance of the rainforests?
原文对应:The dominant ideas, raised by 64% of the pupils, was that rainforests provide animals with habitats.
所选选项:E. Without rainforests some animals would have nowhere to live.
解析:不了解这种题型的同学初看到这道题,很可能会吓一大跳。9-13题总共才5题,选项居然有16个,而且一个选项比一个选项长。不过认真观察一下,其实这道题目不过就是简答题,只是多了选项的简答题而已。所以解题的时候不妨以简答题的思路去做题,再加上其中9-12题都有个共同词——most, 而most最多在文中要怎么体现?是不是多以数字陈列的形式来说明,尤其以比例居多?那么做题时就可以优先查看文中有数字,尤其比例出现的地方是否有题目中的定位词the importance of the rainforests, 这样是不是能更快定位到相关地方呢?然后再对照比对,选出最合适的选项E。
2.真题还原:Cambridge 6 Test 1 Passage 2 Delivering the Goods Question 17 Which paragraph contains the following information?
原题摘录:the weakening relationship between the value of goods and the cost of their deliver
原文对应:As a result, less transportation is required for every dollar’s worth of imports or exports.
雅思阅读如何区别FALSE和NOT GIVEN
FALSE
1. 题目偷换原文概念
原文:
It was named the Silk Road after its most precious commodity, which was considered to be worth more than gold.
题目:
Gold was the most valuable material transported along the Silk Road.
分析:
原文意思是丝绸是最贵的商品,而题目意思是黄金是最有价值的物品。该题虽然没有出现反义词,但是根据原文就可以明确推断出最贵的商品是丝绸,而不是黄金.因此题目张冠李戴,答案选FALSE。
2. 题目和原文信息相反
原文:
These gondolas always weigh the same, whether or not they are carrying boats.
题目:
The weight of the gondolas varies according to the size of being carried.
分析:
题目中的varies与原文中的same构成反义词,两个词表达的含义截然相反,所以答案选FALSE。
上面我们分析了FALSE题的命题规律,相信大家对于遇到那种类型的题选FALSE有了一定的理解。但是呢,又有很多同学把很多FALSE题与NOT GIVEN题混淆,他们都单纯地认为NOT GIVEN是在文中找不到信息,其实这样的理解可以说是基本正确,但是仍然没有认识到NOT GIVEN背后的其它命题规律。接下来,我们再看看这类题怎么做吧~
NOT GIVEN
1. 原文大范围,题目小范围
原文:
The tourist mainly comes from Europe
题目:
The tourist mainly comes from the UK
分析:
欧洲和英国是具有“包含关系”的两种概念,原文说游客来自欧洲 - 大范围,而题目说游客来自英国 - 小范围,那么原文信息中游客来自欧洲,他们有可能来自英国,也有可能来自法国、意大利等等其它欧洲国家,因此题目中游客来自英国只是原文的一种可能性,我们无法判断其正误,所以答案是NOT GIVEN。
2. 根据原文信息无法推断题目描述的关系
原文:
Lower secondary schools in Japan cover three school years, from the seventh grade (age 13) to the ninth grade (age 15). Virtually all pupils at this stage attend state schools: only 3 per cent are in the private sector. Schools are usually modern in design, set well back from the road and spacious inside.
题目:
Private schools in Japan are more modern and spacious than state-run lower secondary schools.
分析:
虽然题目中的Private school和lower secondary schools都提到了,modern and spacious也提到了,但是题目中的比较关系more than根据原文信息无法推断,所以答案就是NOT GIVEN。
3. 题目信息在原文中没有提及
原文:
On the other hand, dams, aqueducts and other kinds of infrastructure will still have to be built, particularly in developing countries where basic human needs have not been met. But such projects must be built to higher specifications and with more accountability to local people and their environment than in the past. And even in regions where new projects seem warranted, we must find ways to meet demands with fewer resources, respecting ecological criteria and to a smaller budget.
题目:
In the future, governments should maintain ownership of water infrastructures.
分析:
原文只提到了water infrastructures,和governments和ownership并没有什么关系,因此选NOT GIVEN。
好啦,到这里大家应该会发现我们做雅思阅读判断题时,最重要的一点就是:做题的依据一定来自于原文信息,而不是自己的脑补!
最后,我们来总结一下判断题中FALSE和NOT GIVEN的解题思路吧:
题目信息与原文不同或者相反,答案是FALSE
题目是原文中的一种可能性,或者根据原文无法判断题目信息,就选NOT GIVEN
【雅思阅读模拟】雅思考试阅读精选及答案详解
带来雅思阅读精选之"Hackers target the home front",文章摘自卫报(The Guardian)。所有雅思阅读方法技巧都需要反复做题去巩固,自己不足的地方也只有通过做题才能显现。练习也是有技巧的,不能盲目瞎做。把每一次阅读练习都当做考试,时间一个小时,三篇阅读,没有手机,没有字典,没有参考资料,没有笔记。只有这样,在考场上才有可能在50分钟内做完题目(十分钟的誊写答案以及检查时间)。强势推广:雅思阅读精品资料,右手边戳链接→_→防脱发秘笈之——雅思阅读精读资料(广而告之,攒人品,爆高分)
题目答案在第二页,自行查阅。听说,每天练习一篇雅思阅读的小伙伴都心想事成了呢。
1.雅思阅读材料
Hackers target the home front
1. One of the UK's leading banks has been forced to admit that organised hacking gangs have been targeting its executives. For the past year, Royal Bank of Scotland has been fighting systematic attempts to break into its computer systems from hackers who have sent personalised emails containing keyloggers to its senior management. This has included executives up to board level and is now the subject of a separate investigation by the Serious and Organised Crime Agency.
2. The hackers are homing in on the trend for people to work from home. The hackers make the assumption that the computers being used outside the work environment are more vulnerable than those protected by a corporate IT department.
Growing threat
3. For companies it is a growing threat as home working increases: a recent survey from the Equal Opportunities Commission found that more than 60% of the UK's population wants the option of flexible working.
4. And the hackers are employing increasingly sophisticated techniques. Each email they send is meticulously built to make it attractive to its target, who the criminals have carefully researched by trawling the internet for information. Once the email is composed, the malware is just as carefully designed: it is often modified to avoid detection by security software.
5. The keylogger contained in the email installs itself automatically and then collects details of logins and passwords from the unsuspecting user. This means that hackers can, using the usernames and passwords stolen by the keyloggers, connect to ___s, or Virtual Private Networks, which many companies use to create an encrypted pathway into their networks.
6. Once inside a bank's network, the hackers can communicate directly with computers holding account information and manipulate funds.
7. Has this actually happened? In some cases sources claim that the login details of have been obtained and used though there has been no confirmation that any losses have occurred as a result. The attacks are not believed to have focused on RBS but to have been across the whole of the banking industry.
8. Royal Bank of Scotland said that the bank had suffered no losses as a result of the attacks and added: "RBS has extremely robust processes in place in order to protect our systems from fraud. Trojan email attacks are an industry-wide issue and are not isolated to a particular area or a particular bank."
9. It is not just banks that have been targets. Last year attempts were made to steal information from the Houses of Parliament using malicious email. Messagelabs, the company responsible for monitoring much of the email traffic of the government and big business for suspect software, said at the beginning of the year that criminals have been evolving more sophisticated techniques to attack corporate networks.
10. According to Mark Sunner, chief technology officer of Messagelabs, the number of malicious emails targeted at individuals has been increasing. Two years ago they were being seen once every two months, but now they are seeing one or two a day. This has been accompanied by an increase in quality in the creation of Trojans and spyware.
11. "The hackers are now aiming to take over computers, particularly those of home users. Some of the malicious software that we are routinely seeing for that purpose will have its own antivirus system built into it so that they can kill off the programs of their competitors."
Increased vigilance
12. Tony Neate, the head of Get Safe Online, a government-funded organisation set up to raise awareness among UK businesses of computer criminals, says: "There is now an attempt to target individuals within UK businesses - including the banking sector. What is happening is that crime is doing what it always does, which is look for the weakest link. Home working is where they perceive a weakness.
13. "This points to a need for increased vigilance and security by those working from home and by those responsible for letting them work from home. For home working to be effective, security needs to be as effective as if working in an office."(667 words)
2.雅思阅读题目
Questions 1-4 Answer the questions below using NO MORE THAN THREE WORDS from the passage for each answer.
1. What do the hackers use to attack the computer system of the Royal Bank of Scotland?
2. Which word is most likely to be used by hackers to describe home computers?
3. What do the majority of people in the UK prefer?
4. How do hackers collect information so as to compose emails?
5. What do hackers obtain illegally to gain access to banks’ computer network?
Questions 5-12 Complete the sentences below with words from the passage.
Use NO MORE THAN THREE WORDS for each answer.
6. The use of login details of ___s by criminals does not necessarily result in any ______________.
7. Royal Bank of Scotland claimed that they are not the only victim of ______________.
8. Corporate networks will be another target of hackers with improved _______________.
9. The attacks on individuals have been greatly increased within _______________.
10. With ________________, software used by criminals can eliminate its competing programs.
11. Home users are chosen as a target because they are considered as a __________ .
12. Get Safe Online is calling for an increase in _____________ to ensure safe home working.
Answers Keys:
1.答案:personalised emails/keyloggers (见第1段第2句:For the past year, Royal Bank of Scotland has been fighting systematic attempts to break into its computer systems from hackers who have sent personalised emails containing keyloggers to its senior management.)
2.答案:vulnerable (见第2段: The hackers make the assumption that the computers being used outside the work environment are more vulnerable than those protected by a corporate IT department. )
3. 答案: flexible working (见第3段: For companies it is a growing threat as home working increases: a recent survey from the Equal Opportunities Commission found that more than 60% of the UK's population wants the option of flexible working.)
4. 答案:trawling (the) internet (见第4段第2句: Each email they send is meticulously built to make it attractive to its target, who the criminals have carefully researched by trawling the internet for information.)
5. 答案: logins and passwords/usernames and passwords (见第5段第第1、2句:The keylogger contained in the email installs itself automatically and then collects details of logins and passwords from the unsuspecting user. This means that hackers can, using the usernames and passwords stolen by the keyloggers, …)
6. 答案: losses (见第7段第2句:In some cases sources claim that the login details of ___s have been obtained and used though there has been no confirmation that any losses have occurred as a result.)
7. 答案: Trojan email attacks (见第8段最后1句:Trojan email attacks are an industry-wide issue and are not isolated to a particular area or a particular bank.)
8. 答案:techniques (见第9段最后1句: …said at the beginning of the year that criminals have been evolving more sophisticated techniques to attack corporate networks. )
9. 答案:two years (见第10段第1、2句:According to Mark Sunner, chief technology officer of Messagelabs, the number of malicious emails targeted at individuals has been increasing. Two years ago they were being seen once every two months, but now they are seeing one or two a day.)
10.答案:(an) antivirus system (见第11段: "The hackers are now aiming to take over computers, particularly those of home users. Some of the malicious software that we are routinely seeing for that purpose will have its own antivirus system built into it so that they can kill off the programs of their competitors." )
11. 答案:weakness (见第12段最后1句: Home working is where they perceive a weakness. )
12. 答案:vigilance and security (见第13段:"This points to a need for increased vigilance and security by those working from home and by those responsible for letting them work from home. For home working to be effective, security needs to be as effective as if working in an office."
雅思阅读技巧之暗示词相关文章:
★ 雅思听力选择题面对干扰项应该怎么做
雅思阅读技巧之暗示词
上一篇:雅思阅读如何搞定判断题
下一篇:雅思阅读配对题的应对策略